What if a single cyberattack could freeze operations and put critical data at risk overnight? As Malaysia accelerates its digital economy, enterprise face threats that are faster, smarter, and more damaging than ever. The stakes are no longer about “if” but “when.”
Recognizing this urgency, Malaysia enacted the Cyber Security Act 2024, which came into force on 26 August 2024 (PWC Malaysia). The act requires organizations in National Critical Information Infrastructure (NCII) sectors to perform risk assessments, audits, incident reporting, and adhere to strict codes of practice. Compliance meetings are now mandatory, serving as both a legal obligation and a business-critical safeguard.
By adopting the 12 pillars of cybersecurity, Malaysian enterprises can align with this new law, safeguard operations, and embrace digital transformation with confidence.
Why a Pillar-Based Approach is Key to Enterprise Cybersecurity?
The cybersecurity landscape is shifting. Attackers exploit gaps left by traditional, single-point tools. Firewalls and antivirus remain important, but they are not enough to protect today’s complex enterprise environments.
A pillar-based approach means no blind spots. It systematically strengthens every critical layer of the business—from disaster recovery to third-party risk—so organizations can respond faster, reduce vulnerabilities, and ensure compliance.
Malaysia’s Expanding Digital Threats
Cyberattacks in Malaysia are evolving from simple malware to advanced strikes targeting cloud workloads, APIs, and supply chains. A recent Gartner report reinforces this trend, revealing that 44% of organizations will substantially increase investment in supply chain cybersecurity this year.
Businesses must defend not only their own infrastructure but also the broader digital ecosystem that keeps operations running, strengthening every layer of defense to stay ahead.
Single-Point Tools Aren’t Enough for Resilience
Standalone tools can’t keep pace with attackers who exploit weaknesses across multiple attack surfaces. A firewall may protect networks but leave endpoints exposed. Antivirus software can detect malware but often misses API threats. Third-party integrations, meanwhile, frequently go unmonitored. The result is fragmented defenses that create higher risks of breaches.
To close these gaps, enterprises need a holistic model that covers every security domain. This is where the 12 Pillars of Cybersecurity come in—a comprehensive framework designed to secure an organization’s entire IT landscape.
Key pillars include:
- Disaster Recovery
- Authentication & Authorization
- Encryption
- Vulnerability Management
- Audit & Compliance
- Network Security
- Endpoint/Terminal Security
- Emergency Response
- Container Security
- API Security
- Third-Party Risk Management
Implementing all 12 pillars ensures that organizations protect data, systems, and operational efficiency. This comprehensive coverage allows Malaysian enterprises to confidently adopt digital transformation initiatives while minimizing risk.
Understanding the 12 Pillars of Enterprise Cybersecurity
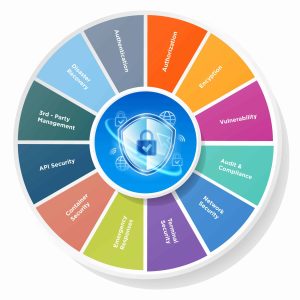
Each pillar represents a critical security domain. Strength comes not from one or two, but from how they reinforce each other across the enterprise. Together, they create a framework that balances prevention, detection, and response.
Disaster Recovery, Authentication, Authorization, and Encryption
These foundational pillars keep businesses resilient in times of crisis. Disaster recovery ensures operations continue during downtime, while authentication and authorization verify every user and device. Encryption adds another layer, protecting data in storage and transit—even if systems are compromised.
Vulnerability Management, Audit & Compliance, and Network Security
A strong security posture requires continuous monitoring. Vulnerability management closes gaps before attackers can exploit them, audit and compliance align operations with regulations, and network security safeguards communications across internal and external systems.
Protecting Endpoints, Cloud Workloads, and Third-Party Connections
Modern enterprises need protections that extend to every layer. Endpoint security shields devices that connect to core systems, while emergency response accelerates containment during incidents. Container and API security protect cloud-native workloads, and third-party risk management ensures suppliers and partners do not become weak links.
Also Read: Things You Need to Know About Denial-of-Service Attack
CTM Solutions to Reinforce Enterprise Cybersecurity

CTM provides enterprise-grade solutions that reinforce the 12 pillars, integrating advanced technology with people and processes to deliver measurable protection and compliance.
Defenxor SOC → Audit & Compliance, Vulnerability, 3rd-Party Risk Management
Defenxor delivers continuous 24/7 monitoring supported by proprietary threat intelligence and in-house R&D to detect advanced threats. With its view-only data access approach, Defenxor strengthens regulatory compliance, minimizes breach risks, and provides enterprises with comprehensive visibility into evolving cyber challenges.
EasiShare → API Security, Container Security, Secure Data Collaboration
EasiShare offers an enterprise-ready collaboration platform with end-to-end encrypted file sharing, detailed activity tracking, and seamless integration with enterprise authentication systems. By protecting sensitive data and ensuring full auditability, EasiShare helps organizations achieve secure collaboration while meeting regulatory requirements.
HCL AppScan & BigFix → Application Security, Endpoint/Terminal Security, Compliance Readiness
HCL AppScan enables organizations to detect weaknesses early in the software development lifecycle through SAST, DAST, and IAST scanning, strengthening application security from the ground up. Complementing this, HCL BigFix provides enterprise-wide endpoint visibility, automated patch management, and compliance enforcement across hybrid environments. Combined, AppScan and BigFix reduce operational costs, minimize risks, and build digital trust across enterprise systems.
Practical Steps for Implementing the 12 Pillars
Understanding the 12 pillars is only the beginning. To achieve real protection, organizations must benchmark their readiness, take structured action, and monitor progress continuously. This ensures that the framework moves from theory to measurable defense.
How Malaysian Enterprises Can Benchmark Against All 12 Pillars
Businesses can assess their current security frameworks against the 12 pillars to reveal gaps in coverage, compliance, and operational effectiveness. Such benchmarking helps leaders prioritize initiatives and allocate resources where they matter most.
Where CTM Solutions Provide the Strongest Defense
CTM (Computrade Technology Malaysia), a leading provider of enterprise cybersecurity solutions, addresses high-risk domains such as application weaknesses, endpoint management, and third-party exposure. By combining actionable insights with automated safeguards, CTM reduces attack surfaces and strengthens enterprise resilience.
Complementing CTM With Other Security Measures for a Full Framework
While CTM covers critical pillars, additional measures like employee training, phishing simulations, and continuous monitoring ensure a robust and layered cybersecurity approach. Integrating these elements reinforces enterprise resilience.
Staying Ahead of Next-Generation Cyber Threats
Malaysian enterprises must prepare today for the risks of tomorrow. AI-driven attacks, cloud-first workloads, and increasingly complex supply chains demand proactive defense strategies. The 12 pillars framework provides a future-ready foundation that evolves with these challenges.
Aligning with Malaysia’s National Cybersecurity Strategy (NCSP)
The 12 pillars are directly aligned with NCSP priorities, enabling enterprises to strengthen both organizational and national resilience. By embedding these principles, companies contribute to Malaysia’s broader digital security agenda.
Meeting Global Compliance Standards
International frameworks such as ISO 27001, GDPR, and HIPAA is essential for businesses with global ambitions. Achieving compliance builds trust, protects partnerships, and opens doors to international markets.
Preparing for AI-driven and Cloud-First Threats
From API exploits to AI-powered phishing, emerging risks demand real-time monitoring and adaptive defense. Organizations that integrate AI-driven protection with cloud security measures gain the agility to respond at market speeds.
Secure Your Business Future with Computrade Technology Malaysia
CTM (Computrade Technology Malaysia) provides end-to-end cybersecurity solutions built on the 12 pillars, combining advanced technologies, advisory services, and regional expertise to protect enterprises across all layers of defense.
Expertise Across Critical Pillars
CTM specializes in strengthening key domains—including endpoints, applications, networks, identity governance, and compliance—ensuring that no critical area is left vulnerable.
Scalable Partnerships
Through partnerships with global leaders like HCL, and proprietary platforms such as Defenxor SOC and EasiShare, CTM delivers solutions that adapt to the evolving needs of enterprises as they scale.
Tailored Roadmaps for Malaysian Enterprises
From initial assessment to deployment and continuous monitoring, CTM builds strategies that align security with business growth, enabling organizations to innovate with confidence.
As part of the CTI Group, CTM brings regional strengths and proven expertise across Southeast Asia, helping enterprises accelerate digital transformation while maintaining compliance and resilience.
Contact CTM through this link to strengthen your cybersecurity posture and secure your enterprise for the future.
Author: Moyna Farla Tsabitah



